Bionic, a CrowdStrike company
The pioneer in Application Security Posture Management (ASPM)
The pioneer in Application Security Posture Management (ASPM)
See threat exposure on every application attack surface.
Lack visibility into your applications and APIs?
Developers deliver new code every day, introducing new attack surfaces which need to be secured.
Thousands
of code changes per day
Hundreds
of hidden attack surfaces
Zero
visibility into apps and APIs
Why choose Bionic?
See and secure every application and API.
Watch the two-minute video
See how Bionic, a CrowdStrike company, automatically discovers and maps all your application dependencies and attack surfaces.
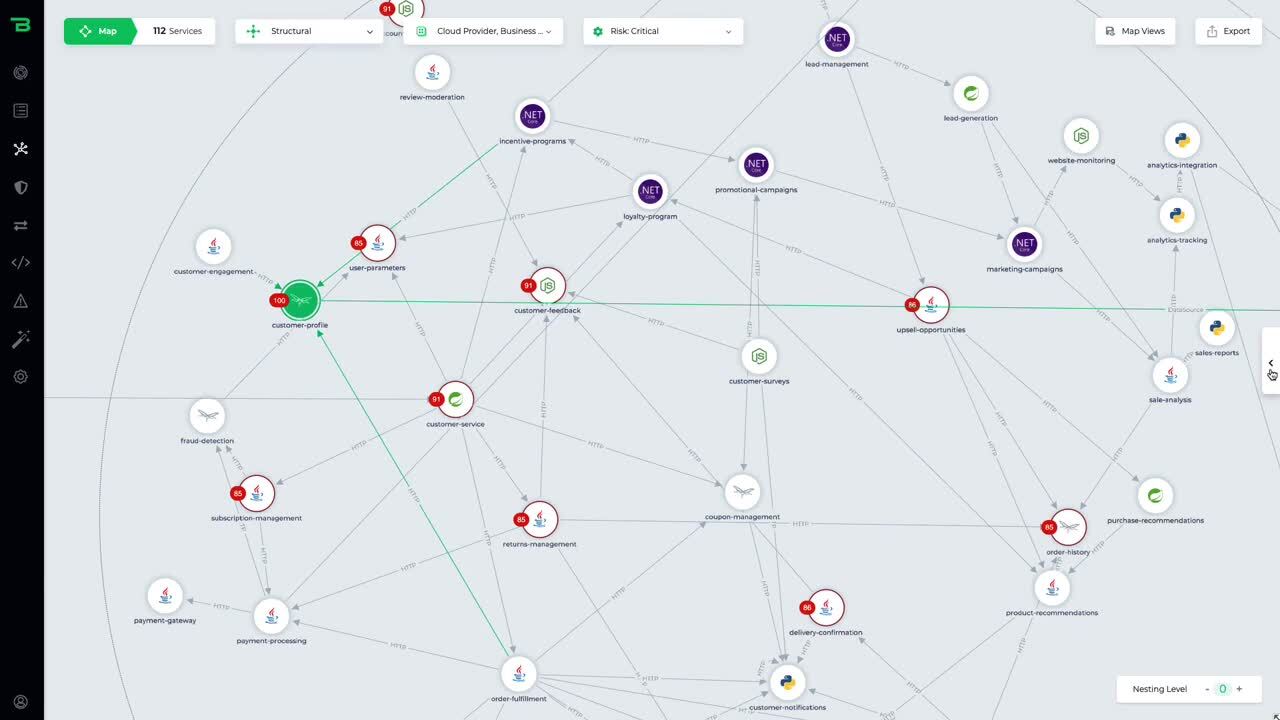
Agentless application discovery and mapping
Get a code-accurate map and a real-time inventory into every microservice, database, API, and dependency running in production. No more outdated CMDB or documentation.
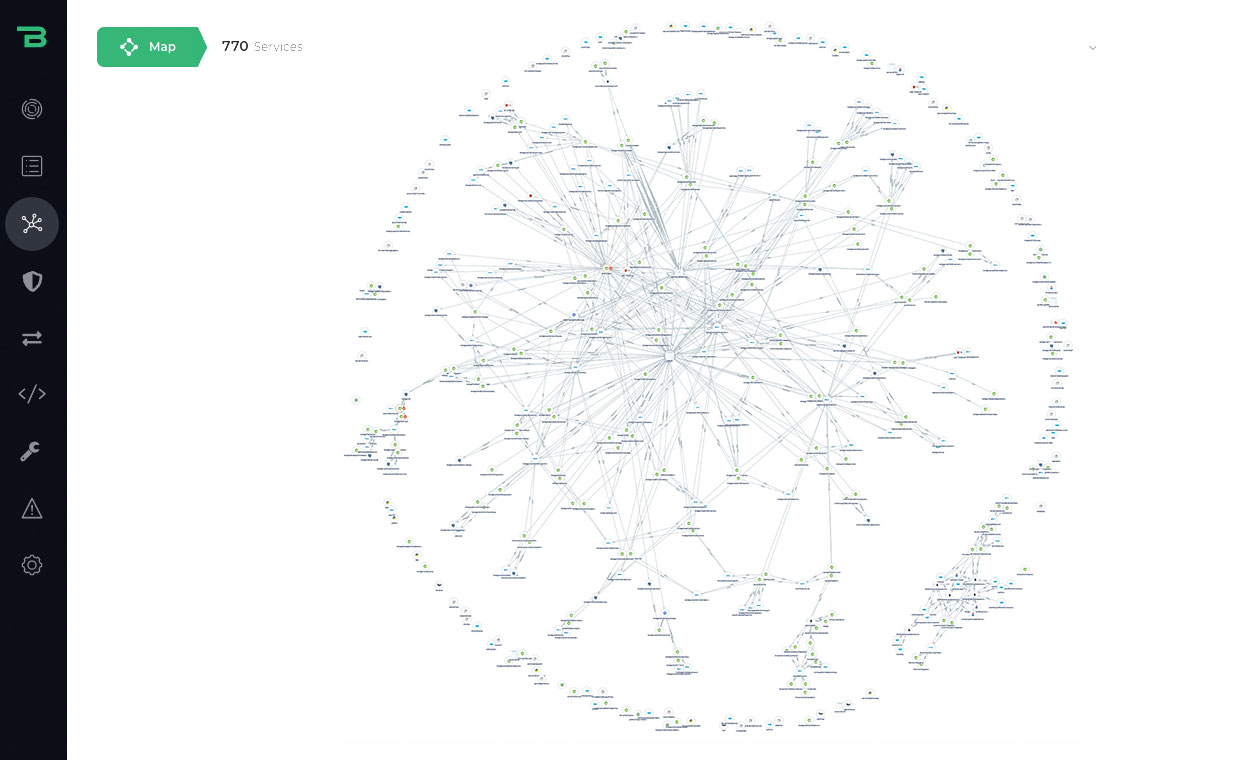
Business context and
risk scoring
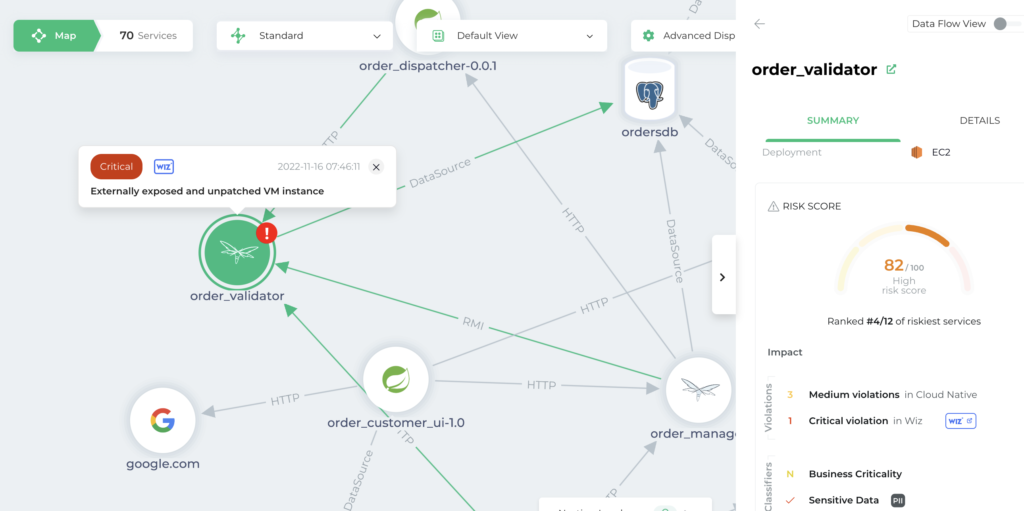
See risk and security through a business lens. CrowdStrike gives you application, business, and cloud context so you know the exact business impact of every threat and vulnerability.
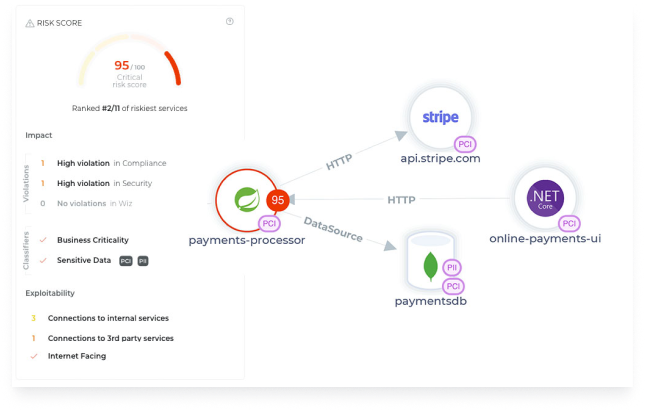
See and secure sensitive data flows
Automatically discover, see, and secure every PII, PCI, and PHI data flow in your production environment. Identify sensitive, internet-facing, and exploitable data flows.
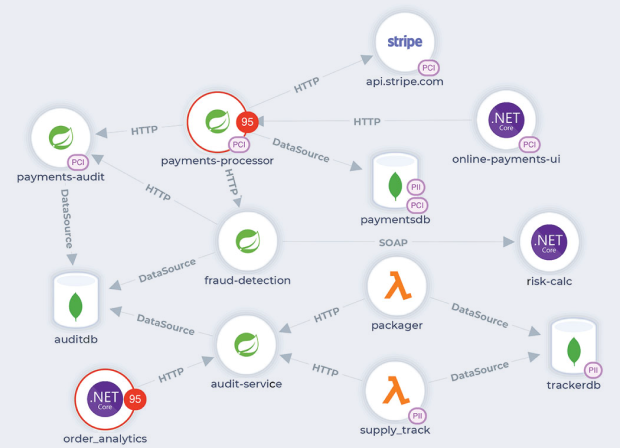
Consolidate threats across your security tools
CrowdStrike integrates with your existing security tools like Wiz and Sonatype so you can consolidate and contextualize threats with your applications.
Automate
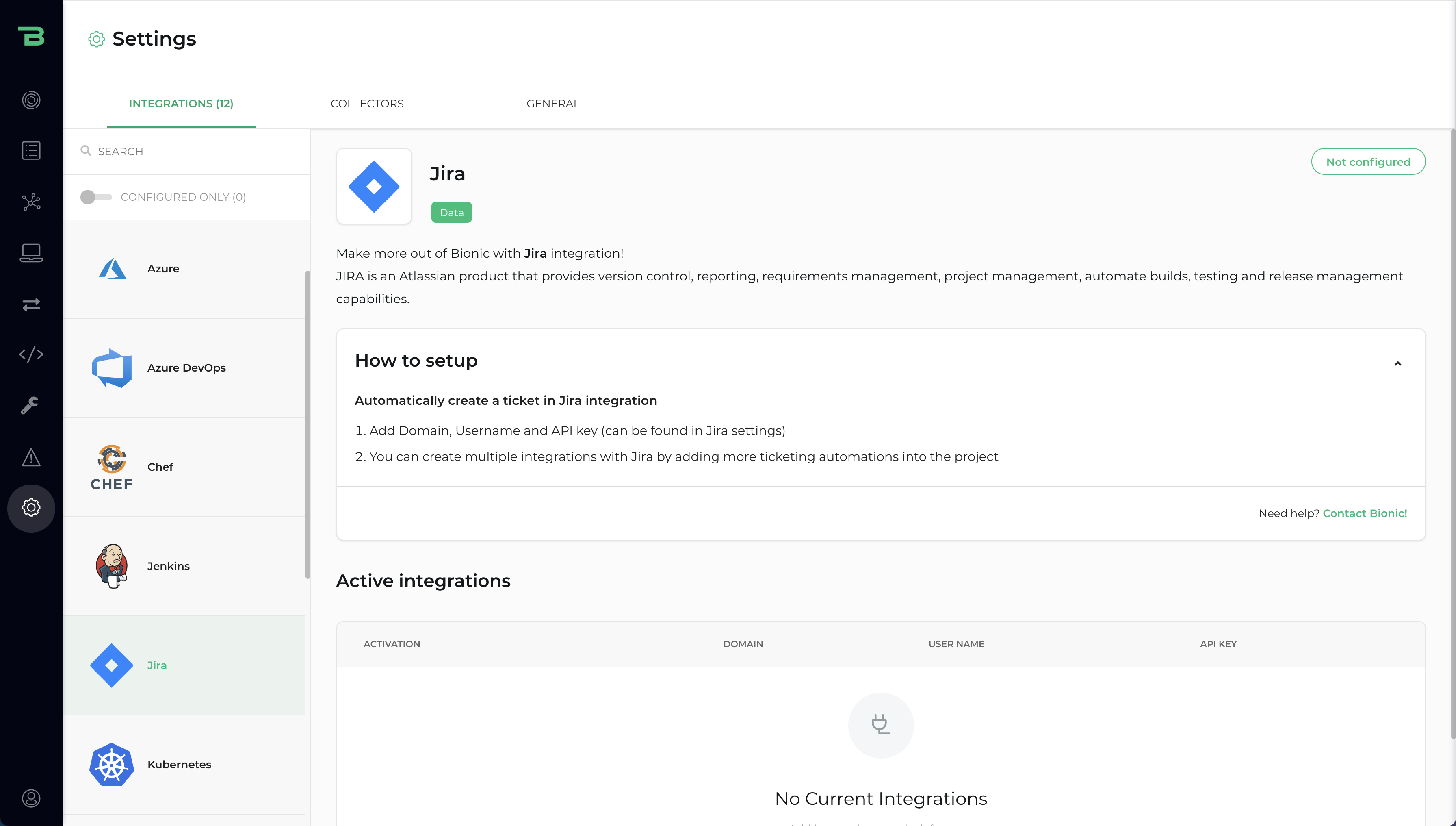
DevSecOps workflows
Automate incident management workflows across security, DevOps, and engineering teams with integrations for Jira, Azure DevOps, and ServiceNow.
See all your applications
and API attack surfaces
Agentless deployment
to get you started in minutes
Complete
visibility
to see things you’ve never seen before
Total
protection
for all of your apps and APIs
Bionic's capabilities
Business risk scoring
With a clear and contextualized risk score that takes into account business impact and use, collective threat severity, data sensitivity, and exploitability, you’ll understand which alerts truly matter.

DevSecOps workflows
Escalate the critical risks into automated workflows through Jira, Azure DevOps, or ServiceNow integration. Give developers more context about what they need to fix, the exact location of the issue, and why this risk is a priority.

Measure and improve your security posture
Use dashboards and reports to show how your security posture is improving over time as you start to secure more applications and APIs.